Apple advanced data protection australia
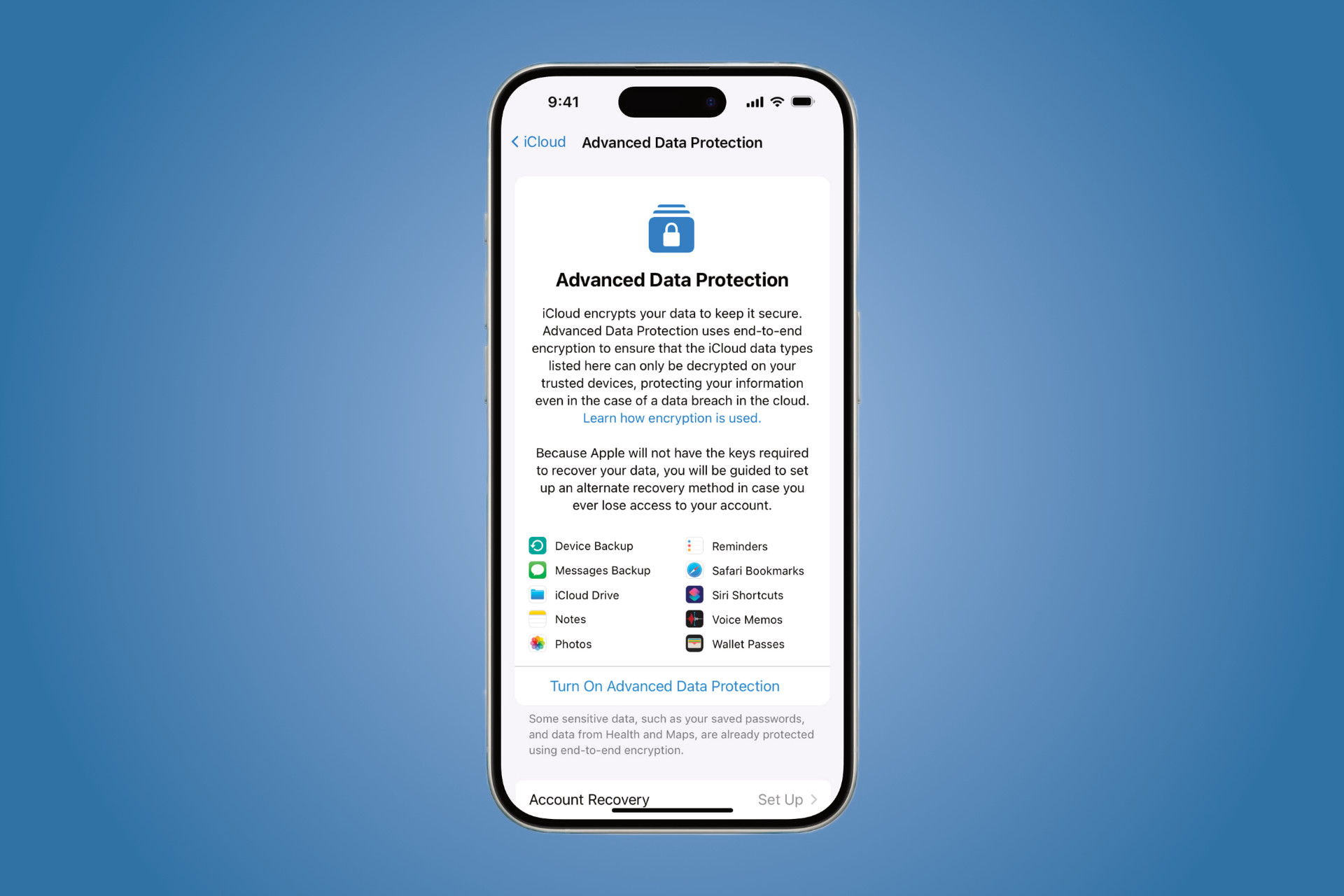
When a user turns on Advanced Data Protection, their trusted devices retain sole access to the encryption keys for the majority of their iCloud data, thereby protecting it with end-to-end encryption. For users who turn on Advanced Data Protection, the total number of data categories protected using end-to-end apple advanced data protection australia rises from 14 to 23 and includes iCloud Backup, Photos, Notes and more. Advanced Data Protection for iCloud will be available to US users by the end of and will start rolling out to the rest of the world in early
Apple today introduced three advanced security features focused on protecting against threats to user data in the cloud, representing the next step in its ongoing effort to provide users with even stronger ways to protect their data. With iMessage Contact Key Verification, users can verify they are communicating only with whom they intend. As threats to user data become increasingly sophisticated and complex, these new features join a suite of other protections that make Apple products the most secure on the market: from the security built directly into our custom chips with best-in-class device encryption and data protections, to features like Lockdown Mode, which offers an extreme, optional level of security for users such as journalists, human rights activists and diplomats. Apple is committed to strengthening both device and cloud security, and to adding new protections over time. Apple pioneered the use of end-to-end encryption in consumer communication services with the launch of iMessage, so that messages could only be read by the sender and recipients. FaceTime has also used encryption since launch to keep conversations private and secure.
Apple advanced data protection australia
A recent report published by Apple has revealed that data breaches have exposed 2. One way is to enable Advanced Data Protection if you have an Apple device. Data breaches have more than tripled in number between and , according to a study conducted by Dr Stuart Madnick from the Massachusetts Institute of Technology. Unfortunately, saw that rate continue to climb. When we think of major Australian incidents, the Optus breach and Medibank hack spring to mind. Hacks, leaks, and breaches will continue to happen but you can minimise their impact on your information such as passwords, health information, and more. Apple says end-to-end encryption is vital to protecting cloud-based data. Simply put, it means that data is only readable on the target devices. Using your phone as an example, you can access passwords on your device, but the online backup is encrypted so that even if the data gets out, no one else can do anything with it. It can only be decrypted by your device. Introduced here with the release of iOS By default, iCloud already uses this type of encryption for data for passwords, payment information, and more. When you turn on Advanced Data Protection, the number of categories that use end-to-end encryption increases from 14 to 23, including information stored on your Notes and Photos apps. Apple has a full list of end-to-end encryption categories on its website.
This metadata is always encrypted but the encryption keys are still stored by Apple. A question for the ages.
Late last year Apple announced several new security focussed features for people who have the strongest concerns about their communications, their data and access to it. Having already launched in the USA, those features are now available in Australia to iOS Beta users, and will be available to all users next week. Apple talks about these features as being important to users such as journalists, human rights activists, politicians and diplomats — just for context. While iMessage is end-to-end encrypted, meaning only the sender and recipient can read the messages on their devices, Contact Key Verification goes one step further allowing people to further verify that it really is the person they think on the other end of the chat. This is done by comparing a contact verification code on each device. The intention is that this is done in person, or over a secure call or video call.
When a user turns on Advanced Data Protection, their trusted devices retain sole access to the encryption keys for the majority of their iCloud data, thereby protecting it with end-to-end encryption. For users who turn on Advanced Data Protection, the total number of data categories protected using end-to-end encryption rises from 14 to 23 and includes iCloud Backup, Photos, Notes and more. Advanced Data Protection for iCloud will be available to U. They are handled like the existing end-to-end encrypted service keys, which means Apple can no longer read or access these keys. Advanced Data Protection also automatically protects CloudKit fields that third-party developers choose to mark as encrypted, and all CloudKit assets. It does so by writing a new value, signed by device-local keys, into its iCloud Keychain device metadata.
Apple advanced data protection australia
Apple today introduced three advanced security features focused on protecting against threats to user data in the cloud, representing the next step in its ongoing effort to provide users with even stronger ways to protect their data. With iMessage Contact Key Verification, users can verify they are communicating only with whom they intend. As threats to user data become increasingly sophisticated and complex, these new features join a suite of other protections that make Apple products the most secure on the market: from the security built directly into our custom chips with best-in-class device encryption and data protections, to features like Lockdown Mode, which offers an extreme, optional level of security for users such as journalists, human rights activists, and diplomats. Apple is committed to strengthening both device and cloud security, and to adding new protections over time. Apple pioneered the use of end-to-end encryption in consumer communication services with the launch of iMessage, so that messages could only be read by the sender and recipients. FaceTime has also used encryption since launch to keep conversations private and secure. Now with iMessage Contact Key Verification, users who face extraordinary digital threats — such as journalists, human rights activists, and members of government — can choose to further verify that they are messaging only with the people they intend. The vast majority of users will never be targeted by highly sophisticated cyberattacks, but the feature provides an important additional layer of security for those who might be.
Strawberry fields amarillo tx
The security feature ensures that only device users and the recipients of messages and files sent by the user can access the data. Both Apple and third-party data centres may be used to store and process your data. Advanced Data Protection also automatically protects CloudKit fields that third-party developers choose to mark as encrypted, and all CloudKit assets. Name, model, colour and serial number of the device associated with each backup. Representative examples are provided in the table below. Contact the vendor for additional information. Second, the device initiates the removal of the available-after-authentication service keys from Apple data centres. Simply put, it means that data is only readable on the target devices. Security companies offer smart technologies — primarily cameras — to protect your home from burglary, fire and other incidents. Official MacBook Air dual display support is finally here. Policymakers in the European Union and U.
When you enable Advanced Data Protection, Apple collects limited information related to your use of the feature and information about account recovery. This information is associated with your Apple ID and is used to improve the feature and to ensure the reliability of the account and data recovery processes.
See all results. When a user first turns on Advanced Data Protection, web access to their data at iCloud. Considering that data stored in the cloud is the majority affected by data breaches, it makes sense to take every reasonable precaution possible. Note: Your account recovery methods are never shared with or known to Apple. Taylor was spending too much time in a new role as Twitter Inc. Apple doesn't access or store keys for any end-to-end encrypted data. Then scroll down and turn off Advanced Data Protection. The keys are always stored and secured in Apple data centres. Yes No. Find out how to turn on Advanced Data Protection for iCloud. At the same time, European officials have aggressively pursued policies designed to increase user privacy and undercut the powers of large tech companies. By default, Apple backups save all information on your device, including iMessage correspondence. The security feature ensures that only device users and the recipients of messages and files sent by the user can access the data. Availability iMessage Contact Key Verification will be available globally in Many police agencies and some politicians, however, respond that end-to-end encryption hampers law enforcement authorities in their efforts to stop child sex abuse, drug trafficking, terrorism, and other crimes.

It is easier to tell, than to make.
What useful question
In my opinion you are not right. I can defend the position. Write to me in PM, we will communicate.