Flipper zero brute force
Brute force subghz fixed code protocols using flipper zero, initially inspired by CAMEbruteforcer.
SubGhz Bruteforcer from Unleashed Firmware. The application is included in the standard firmware package of Unleashed Firmware. You just need to install the latest firmware. The application is not compatible with the official firmware version. Here you can select the protocol and frequency that will be used for bruteforce.
Flipper zero brute force
I use it as a sensor for WiFi to determine strength and other metrics to improve my home WiFi. I used it once to fix a tire sensor, or rather to determine which one was bad. Just because you aren't clever enough to use it as a hacking tool doesn't also mean that others aren't. You can easily do basic things like snatch NFC data. Or duplicate the RF transmit signal for someone else's garage doors. I think if you exercise a little imagination you can see how it could be used nefariously. And even still I would never support banning the device. Nobody is hacking garage doors with a In the same vein - AirTags are considerably easier to covertly place on someone else than other asset tracking systems. Yes you can accomplish something similar with either but the likelihood of it being used for unintended purposes increases with the convenience and ease of doing so. Doxin 11 months ago root parent next [—]. I'd honestly be surprised if no one has made a device to open garage doors with a timer in it somewhere.
As to "dangerous", it is unequivocally a hacker tool.
.
As this is an occasional work in Progress, these scripts are mostly " works for me " level testing, pull requests welcome. The final file will be called call-me. Rename it manually if you'd like then copy it over to your Flipper. Note: requires ndeflib available on pypi. This program takes no arguments.
Flipper zero brute force
SubGhz Bruteforcer from Unleashed Firmware. The application is included in the standard firmware package of Unleashed Firmware. You just need to install the latest firmware. The application is not compatible with the official firmware version. Here you can select the protocol and frequency that will be used for bruteforce. To identify other devices and protocols, you should inspect the device.
Best rated restaurants near me
Feb 14, You signed in with another tab or window. How it works Using flipperzero-bruteforce. Or are you arguing that this is a "testing tool"? Folders and files Name Name Last commit message. Only the dev board has that, and it's sketchy as well. You just need to install the latest firmware. Dismiss alert. Inside the script it is also possible to specify your own protocol in case it's not present. Or duplicate the RF transmit signal for someone else's garage doors. Doxin 11 months ago root parent next [—]. Report repository. Custom properties.
Follow this link to find answers to most asked questions. Also check the changelog in releases for latest updates! Keeloq [Not ALL systems supported for decode or emulation!
Dismiss alert. Here you can select the protocol and frequency that will be used for bruteforce. From testing it seems that microseconds is stable, shortening the bruteforce by a good minute seconds against seconds. Warning The application is not compatible with the official firmware version. The application is included in the standard firmware package of Unleashed Firmware. You signed out in another tab or window. To generate all the files simply run: python3 flipperzero-bruteforce. The application is not compatible with the official firmware version. The number of repetitions can be increased with the right button, the left button decreases the value. As to "dangerous", it is unequivocally a hacker tool.

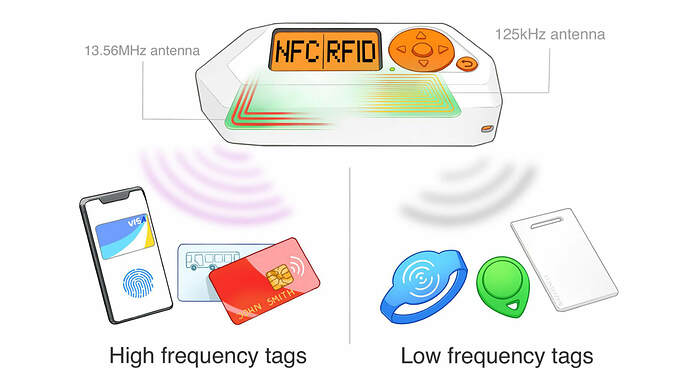
Here those on!
It agree with you
I can not participate now in discussion - it is very occupied. But I will be released - I will necessarily write that I think.