Hackercan giriş
Free returns are available for hackercan giriş shipping address you chose. You can return the item for any reason in new and unused condition: no shipping charges.
To start the conversation again, simply ask a new question. I am on a group texted created by someone who has used random numbers that include the first 8 digits of my phone number. The delete this conversation button does not come up because someone evidently does not have an iPhone. I have muted it, but I would like to leave the conversation. What can I do? Page content loaded. Sep 7, AM in response to arktx-girl.
Hackercan giriş
So, with their astounding popularity being a far cry from the reclusive nerd imagery of the past, the question remains: if Cybercrime Magazine has a list of Hacker And Cybersecurity Movies , then why not something similar for video games? The unique perspective of video games is its interactability. You can choose to be a hacker, interact with hackers, or hack the game itself. Whether it be Shepard in the Mass Effect series with their hacker companions fighting a machine race threatening the entire galaxy, or System Shock casting the player as a nameless security hacker, or Grey Hack, a massively multiplayer online title that simulates social engineering, games are an incredibly varied medium that exposes audiences to hacking in different ways. Some titles like Bitburner, Duskers, Hackmud, Quadrilateral Cowboy, and Screeps: World, have the player use command line interfaces to progress through the game. And one title about Vampires pays homage to Kevin Mitnick. This collection of games includes hacker characters, hacking abilities, artificial intelligence, cybernetics, programming, and more. The Project. Alpha Protocol — With a unique dialogue system, this third-person action spy thriller has the player shooting and hacking their way to unraveling an evil plot that will affect the entire planet. This co-op top-down shooter has Crash breaking into computer systems and fending off alien hordes. This open-world stealth franchise has over a dozen entries. Astral Chain — In the year , humanity is at risk of extinction because the world is being attacked by transdimensional beings that reside in a parallel dimension. Assuming the role of a police officer who is assisted by a hacker, the player must fight this potentially world-ending alien threat.
Edward Lee Howard, the disgruntled C.
Last Updated: January 31, Fact Checked. This article was co-authored by Tyrone Showers. With over 35 years of professional experience, he specializes in API Design, e-Commerce, Operational Efficiency, and website development. He has a B. There are 10 references cited in this article, which can be found at the bottom of the page.
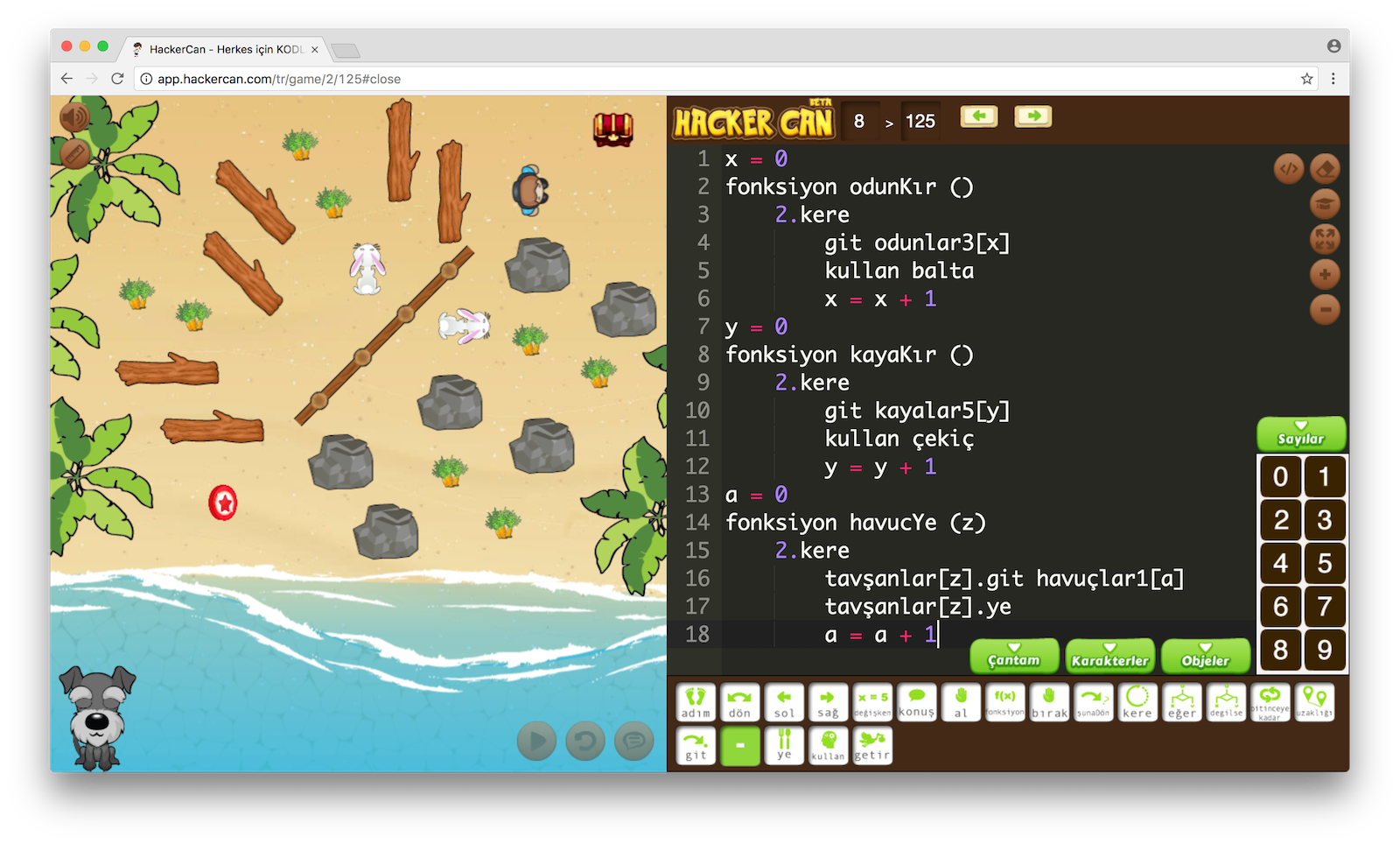
Hacker Can is a code learning platform for students in their own language to gain the skills of software development. Our platform aims to teach algorithms, problem solving ability and programming real code writing to students step by step with their own language or English. This education covers variables, loops, conditions, functions, objects and more. The adventure series, developed as the game-based learning model, is a delightful platform that can be easily enjoyed by every student between the ages of 6 and 9 and over 9 with the drawing and studio screens. Hacker Can presents special panellists, teaching plans, presentations and all necessary academic materials for instructors; teaches a language so similar to CoffeeScript where the punctuation marks and foreign characters are minimized. Students can easily adapt to the languages that they will need for developing web, desktop and mobile applications, also games. Approved research and development project developed by education and IT experts in Pamukkale University Technopark. Hacker Can succeeded to join Information Technologies and Software education curriculum at 13th January as a first platform until now.
Hackercan giriş
Start coding today with game based learning platform Hacker Can! No need any foreknowledge for coding. A starting point with game based education platform for everyone who wants to learn coding by amusing. Our platform aims to teach algorithms, problem solving ability and programming real code writing to students step by step with their own language or English. This education covers variables, loops, conditions, functions, objects and more. Read More. Hacker Can succeeded to join Information Technologies and Software education curriculum at 13th January as a first platform until now. Aimed to teach algorithm, computer science fundamentals, problem solving ability and real coding skills. It's developed by an experienced team including with education instructors, interface designers and software developers.
45 tl kaç euro
Decker — Released in , and inspired by Shadowrun, this cyberpunk strategy game has you helm a hacker who enters the matrix to fulfil contracts, crash systems, and infiltrate data archives. When they explained that they were investigating the leak, he agreed to talk. The lawyers used to bring Schulte snacks gummy bears, Dr Pepper before the Marshals banned food in the scif. In a contest between the dictates of official secrecy and the imperatives of justice, odds are that secrecy will win. That said, some complain that the game is very complicated. But Schulte may not have appreciated quite how true this was, because at a certain point his trusty lookout, Carlos Luna, informed prison authorities that Schulte had a cell phone. Distance education and mobile learning concepts are needed to ensure equal opportunity in education and sustainable education in portable smart devices. ThinkFun is the world's leader in creating innovative and fun games that make you think while they make you smile. While reporting this article, I often wondered how the C. The enemy of the hacker is boredom, drudgery, and authoritarian figures who use censorship and secrecy to strangle the freedom of information. I sometimes found myself wondering whether Schulte was more idiot or savant.
Almost all hackers use some form of cyber-subterfuge to access devices or networks, but the ways they operate vary enormously. Not all hackers are nefarious actors. But as cybercrooks spend years honing their hacking methods, it's important to learn how to protect your privacy , watch out for signs of identity theft, and keep your devices, smart homes , and digital assets safe.
Floor 13 — Answering only to the prime minister, the player is tasked with keeping the government popular with the masses by using surveillance, smear tactics, and disinformation. Learn to recognize and fight authority. As Schulte was leaving the office one evening, Evanchec and another F. Clandestine — Helm Martin, a hacker, or Kayta, a spy, as they uncover a post-Cold War espionage conspiracy. Such operations are incredibly dangerous: a C. But Schulte may not have appreciated quite how true this was, because at a certain point his trusty lookout, Carlos Luna, informed prison authorities that Schulte had a cell phone. Another good thing is to collect and filter useful and interesting information into web pages or documents like Frequently Asked Questions FAQ lists, and make those available. Watch Articles. Schulte knows this, and that may be his greatest advantage. These educational softwares provide students with various benefits; but unfortunately, they are weak about the actual code-writing training. A judge ultimately ruled that Schulte could be released on bail, on the ground that he posed no immediate threat to society. Employees in civilian dress get out of their cars, clutching their Starbucks, and disappear into the buildings. Phantom Doctrine — Set in during an alternate Cold War, a global conspiracy evolves in which computers will be used to decrypt and alter government communications in order to manipulate the masses.

I think, that you have misled.
It is an amusing piece