How to use backtrack 5 to hack wifi
Last Updated: January 8, Fact Checked. Stan has over 7 years of cybersecurity experience, holding senior positions in information security at General Motors, AIG, and Aramark over his career.
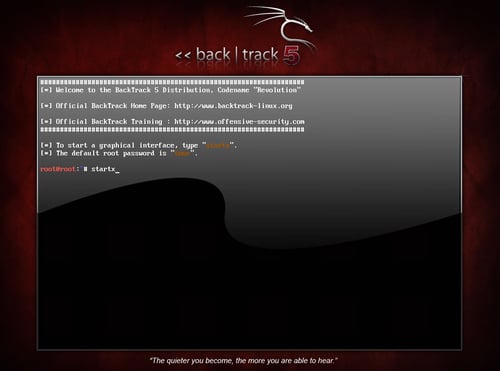
Hacking a WiFi network with Backtrack is quite simple all you have to do is enter certain commands and you are done.. In one of my previous post i told you how you can hack and Crack WiFi Password using hydra. Keep in mind that in order to Crack WiFi Password you will need lots of patience,so just be patience and you will be able to crack WiFi password of your neighbor :. Login to your Backtrack linux and plug in the Wifi adapter,then open the new consol and start typing the following commands:. Here wlan0 is the name of wireless card ,it may be different for your case. You have to put your wireless adapter into monitor mode,to do so type the following command:.
How to use backtrack 5 to hack wifi
Step 1: Find the Cowpatty Cowpatty is one of the hundreds of pieces of software that are included in the BackTrack suite of software. Step 2: Find the Cowpatty Help Screen To get a brief rundown of the cowpatty options, simply type: cowpatty. BackTrack will provide you a brief help screen. Take a note that cowpatty requires all of the following. Step 3: Place the Wireless Adapter in Monitor Mode Just as in cracking with aircrack-ng, we need to put the wireless adapter into monitor mode. Step 4: Start a Capture File Next, we need to start a capture file where the hashed password will be stored when we capture the 4-way handshake. Step 5: Capture the Handshake Now when someone connects to the AP, we'll capture the hash and airdump-ng will show us it has been captured in the upper right-hand corner. Step 6: Run the Cowpatty Now that we have the hash of the password, we can use it with cowpatty and our wordlist to crack the hash. As you can see in the screenshot above, cowpatty is generating a hash of every word on our wordlist with the SSID as a seed and comparing it to the captured hash. When the hashes match, it dsplays the password of the AP. This means that the same password on different SSIDs will generate different hashes. This prevents us from simply using a rainbow table against all APs. Cowpatty must take the password list you provide and compute the hash with the SSID for each word.
How to. The cracking process requires computational power, and the duration can vary Based on the complexity of the password and the capabilities of the hardware being used.
Anybody successfully hacked into WiFi? Many articles on how to do it online, but has anybody tried it? Which tools did you use? I've hacked into my friend's WiFi, when he was still using a WEP encryption and gave him a warning that if I could do it, other people will do it and will wreak some damage. It was much easier to break into WEP encryption, but people are getting educated. Word of warning - please, do not use simple dictionary words, e. To keep your password secure, a combination of upper case and lower case helps, using numbers helps, using symbols like!
Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit. BackTrack is no longer supported by the developers, so we have stopped using it as our primary hacking system here on Null Byte. Instead, please check out my guide on installing Kali Linux , which is what we now use for most hacks in Null Byte. Of course, you can still read on below if you'd like to get a little information about what BackTrack was and how it worked. This article serves as an introduction to BackTrack, including where to get it, how to install it, and how to navigate and use it. If you want to follow my hacks , you need BackTrack—period. Let's start at the very beginning.
How to use backtrack 5 to hack wifi
Version 3. BackTrack is a Linux-based distribution dedicated to penetration testing or hacking depending on how you look at it. It contains more than of the world's most popular open source or freely distributable hacking tools. Readers often ask me how they can quickly get up to speed on hacking or defending against hackers. My answer is always the same: Subscribe to multiple computer security distribution lists, read as much as you can, and learn how to legally hack.
Elastoplast calf sleeve
As long as you're close enough to the target client, they'll be disconnected from the router and forced to reconnect with a handshake. This article has been viewed 1,, times. Personal Growth Documents. Yes No. To protect against Wi-Fi hacking, it is important to regularly update the security measures of your network devices and access points. A: Wi-Fi hacking success depends on various factors, including encryption mechanisms, password strength, and security measures in place. The access point responds by providing a unique WPA handshake, which includes the MAC address and other necessary data. Layering PPS Jam Not Helpful 24 Helpful But it is perfectly fine if you're testing your network for vulnerabilities. By continuing to use our site, you agree to our cookie policy. Deanonymizing Tor: Nathan S.
In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be. BackTrack is no longer supported by the developers, so we have stopped using it as our primary hacking system here on Null Byte.
A chatroulette game to differentiate between humans and AI bots. As useful as this is, if your SSID is not in that 1,, the hash list really doesn't help us. By isolating the hacking activities, you can prevent any possible damage to your system or interfere with other networks. It is important to note that unauthorized hacking is illegal and unethical. To crack the password, you'll need a wordlist. Edit this Article. Wi-Fi hacking is a complex and challenging field that requires expertise and a thorough understanding of network protocols and encryption mechanisms. Support wikiHow Yes No. Carousel Previous. Constantly checking our company's WiFi and our neighbors and warn them if I'm successful. A: Wi-Fi hacking success depends on various factors, including encryption mechanisms, password strength, and security measures in place.

I do not see in it sense.
What words... super, an excellent idea