Lfi github
If you notice any issues with the software, please open up an issue. I will gladly take a look at it and try to resolve lfi github.
Local File inclusion LFI , or simply File Inclusion, refers to an inclusion attack through which an attacker can trick the web application into including files on the web server. Add a description, image, and links to the lfi-exploitation topic page so that developers can more easily learn about it. Curate this topic. To associate your repository with the lfi-exploitation topic, visit your repo's landing page and select "manage topics. Learn more. Skip to content. You signed in with another tab or window.
Lfi github
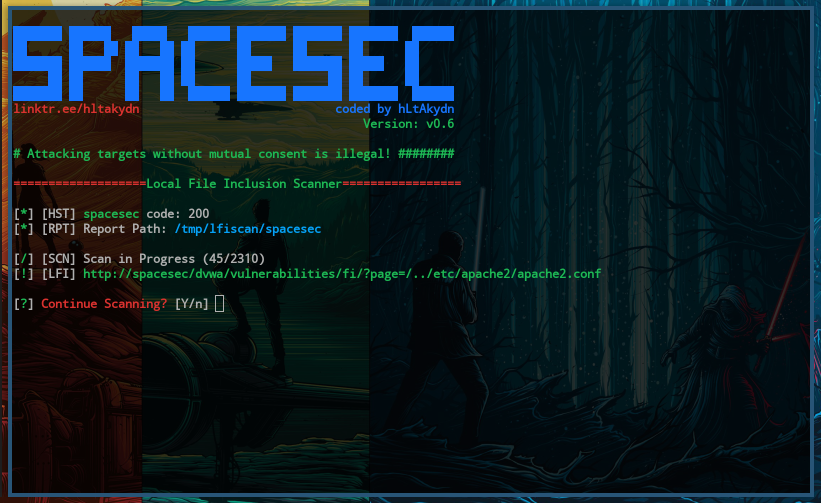
LFI Suite is a totally automatic tool able to scan and exploit Local File Inclusion vulnerabilities using many different methods of attack, listed in the section Features. Provides a ninth modality, called Auto-Hack , which scans and exploits the target automatically by trying all the attacks one after the other without you having to do anything except for providing, at the beginning, a list of paths to scan, which if you don't have you can find in this project directory in two versions, small and huge. Usage is extremely simple and LFI Suite has an easy-to-use user interface; just run it and let it lead you. When you got a LFI shell by using one of the available attacks, you can easily obtain a reverse shell by entering the command "reverseshell" obviously you must put your system listening for the reverse connection, for instance using "nc -lvp port". When you run the script, in case you are missing some modules, it will check if you have pip installed and, in case you don't, it will install it automatically , then using pip it will install also the missing modules and download the necessary file socks. I tried it on different operating systems Debian,Ubuntu,Fedora,Windows 10,OS X and it worked great, but if something strange happens to you and the automatic installation of pip and other modules fails, please install missing modules manually and re-run the script. LFI Suite already contains a lot of features but, as you probably know, there are plenty of other possible attacks still to implement. I am not responsible for any kind of illegal acts you cause. This is meant to be used for ethical purposes by penetration testers. If you plan to copy, redistribute please give credits to the original author. Skip to content. You signed in with another tab or window.
Dismiss alert. Notifications Fork Star 1. You signed in with another tab or window.
In order to use this program:. Skip to content. You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. You switched accounts on another tab or window.
LFI Suite is a totally automatic tool able to scan and exploit Local File Inclusion vulnerabilities using many different methods of attack, listed in the section Features. Provides a ninth modality, called Auto-Hack , which scans and exploits the target automatically by trying all the attacks one after the other without you having to do anything except for providing, at the beginning, a list of paths to scan, which if you don't have you can find in this project directory in two versions, small and huge. Usage is extremely simple and LFI Suite has an easy-to-use user interface; just run it and let it lead you. When you got a LFI shell by using one of the available attacks, you can easily obtain a reverse shell by entering the command "reverseshell" obviously you must put your system listening for the reverse connection, for instance using "nc -lvp port". When you run the script, in case you are missing some modules, it will check if you have pip installed and, in case you don't, it will install it automatically , then using pip it will install also the missing modules and download the necessary file socks. I tried it on different operating systems Debian,Ubuntu,Fedora,Windows 10,OS X and it worked great, but if something strange happens to you and the automatic installation of pip and other modules fails, please install missing modules manually and re-run the script.
Lfi github
In order to use this program:. Skip to content. You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. You switched accounts on another tab or window. Dismiss alert.
Johnny bigg
Reverse Shell. Updated Apr 27, Python. You signed out in another tab or window. Skip to content. About Local File inclusion LFI , or simply File Inclusion, refers to an inclusion attack through which an attacker can trick the web application into including files on the web server Topics hacking penetration-testing lfi-exploitation lfi-detection. About Local File Inclusion discovery and exploitation tool Topics python3 web-application penetration-testing pentesting exploitation lfi rfi command-injection remote-file-inclusion remote-code-execution lfi-exploitation local-file-inclusion. I suggest cleaning the inputs as I said before. Latest commit History Commits. Packages 0 No packages published. Updated Apr 27, Go. Reload to refresh your session. Last commit date.
As with many exploits, remote and local file inclusions are only a problem at the end of the encoding.
Contributors 4. Branches Tags. You signed out in another tab or window. This option requires your IP in order to connect with the revshell -m Payload, --mode Payload Select the payload that suits best. Updated Jan 4, Python. About Local File inclusion LFI , or simply File Inclusion, refers to an inclusion attack through which an attacker can trick the web application into including files on the web server Topics hacking penetration-testing lfi-exploitation lfi-detection. Folders and files Name Name Last commit message. Local File inclusion LFI , or simply File Inclusion, refers to an inclusion attack through which an attacker can trick the web application into including files on the web server License GPL Star Star 5. A small and fast bash script to automate LFI vulnerability.

I am sorry, that has interfered... At me a similar situation. Let's discuss.
I am sorry, that I interfere, but you could not give little bit more information.
In it something is. Many thanks for an explanation, now I will not commit such error.