Putty port knocking
I've been in this business for a long, long time and have come across all manner of innovations regarding network security. Port knocking which I think I learned about first at defcon
Port knocking is a way to secure a server by closing firewall ports—even those you know will be used. Those ports are opened on demand if—and only if—the connection request provides the secret knock. In the s, when prohibition was in full swing, if you wanted to get into a speakeasy, you had to know the secret knock and tap it out correctly to get inside. Port knocking is a modern equivalent. If you want people to have access to services on your computer but don't want to open your firewall to the internet, you can use port knocking.
Putty port knocking
.
If you've got a single system you're managing outside of a cloud provider with its own decent network firewall, just set up WireGuard and filter everything but that.
.
Connect and share knowledge within a single location that is structured and easy to search. How can I have a port knocking sequence or a command that does the port knocking executed prior to trying to establish an SSH connection? Preferably using the pre-installed ssh command, but also willing to switch if there's no "standard alternative". You can also try to use the option ProxyCommand. It gives you the ability to control the command used to connect to the server; sounds troublesome, but I haven't found any problem with it yet. Specifies the command to use to connect to the server. The command can be basically anything, and should read from its standard input and write to its standard output. It should eventually connect an sshd 8 server running on some machine, or execute sshd -i somewhere. Host key management will be done using the HostName of the host being connected defaulting to the name typed by the user.
Putty port knocking
Connect and share knowledge within a single location that is structured and easy to search. Can you please demonstrate how to do the same in Windows. We currently use PuTTY. Is there an alternative?
Rust thesaurus
Treat it first as a source of information: did I screw something up somewhere? Port knocking is great. EvanAnderson on May 15, root parent prev next [—]. Just don't do it. At the point where you're installing network cryptography tools to authorize access to your machine, why not just use a real cryptographic tunnel? There is this idiotic notion that any security measure that cannot stand on its own is "security by obscurity", and therefore useless. Agreed, you can work around that but it's a PITA. Not by anecdotes on the internet. Take a look at fwknop for the implementation. Until you forget your phone at home and proceed to lock yourself out of your apartment with no way to call for help! Hacker News new past comments ask show jobs submit. The point of the honeypot is that there's no heuristic causing any delay or elusive attacker being missed e.
Note that you will require root access in order to use these directions. This tutorial will go over how to use port knocking which will be considered an advanced guide and does require you to have root access and have CSF installed on your server. Port knocking will reduce brute force attacks as it adds a second layer of security to your server.
Pxtl on May 15, prev next [—] This seems brittle as hell, and is security-through-obscurity. There is nothing you can reasonably do to prevent it the sources are so diverse you couldn't even realistically block a determined scanner , and, if you've turned off password authentication which you must do anyways the probes aren't a meaningful threat. Then ssh would protect you. If you're exposing a developer instance to the network and it has port knocking deployed, why does it matter? Port knocking is great theatre but not much good for anything else. Make a note of the name of your connection. It's just a technique to add a layer of protection. Key Takeaways Port knocking is a method of securing a server by closing firewall ports and allowing access only if a specific sequence of connection attempts is made. Easy way to find some shells.. Why is this better than an application taking open requests on one of the ports and accepting a password used to open the other port? If your ssh sever had a 0day, port knocking would protect you. What do you think about single packet authorization? However, you could argue that port knocking doesn't add much if anything to a properly hardened, secure system.

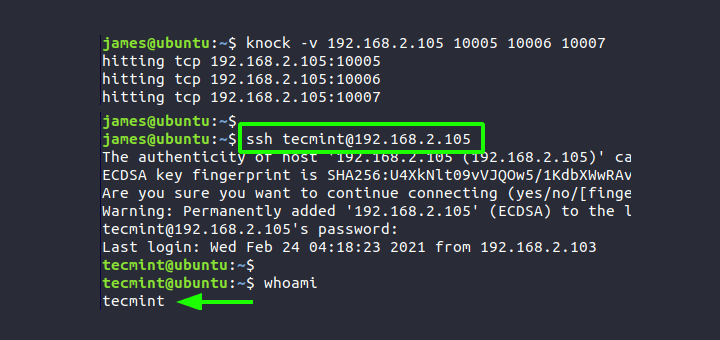
Bravo, seems excellent idea to me is