Slam acronym cyber security
Approximately 8 out of 10 data breaches include a human element. Many reports that point the finger at the human error when it comes to cybersecurity issues, that is.
Phishing is a type of cyber attack that involves tricking someone into giving up sensitive information, such as passwords, client data, financial data, or for the unsuspecting user to download an attachment or visit a link to infect their computer. Cybercriminals typically use email as the primary attack vector. If you want to know more about social engineering attacks on businesses and have 7 minutes, you should watch the following video of Rachel Tobac, CEO of SocialProof Security. As mentioned in the intro of this article, this will be a short and sweet explanation of what SLAM is and how your business can implement it. I receive a spear-phishing attempt once a week.
Slam acronym cyber security
Cybercrime hit the scene in the s as computer information technology IT took shape. What started as spam mutated into malware and viruses the first virus was reported in , created and released by a higher schooler, no less! Remember having to download pop-up blockers and Norton Antivirus software or having your computer crash? Transitioning to cloud-based infrastructures created a cornucopia of critical failure points and security gaps. Not only does this cost billions, but it creates a deadly ripple effect reputationally and legally and can threaten human life in the healthcare setting. While many would argue that cyberattacks can be blamed on one failed password or misconfiguration, hacking happens in stages, making it critical to be vigilant. This article will define some key terms, explain types of email phishing, describe the SLAM method, and provide examples of how to protect yourself. There are four key players in this cyber world:. A large meta-analysis in looked at 70 articles published in the last 12 years on cybersecurity. While several security gaps made the headlines, phishing rose to the top.
CEO Fraud spear-phishing attacks take advantage of their target by sending them an email that appears to be from a known or trusted sender…in most cases their boss. These are all phishing.
Phishing is a social engineering tactic that starts with an email. Social engineering is an attempt to trick the target you or your employees into sharing data, providing access to a system, or taking another action that the scammer can use for illicit gain. Phishing usually starts with an email email phishing , but it can also involve text messages smishing and voice calls or voicemail vishing. These are all phishing. You would think after decades of phishing attacks, companies would have figured out ways to get rid of them completely. But scammers constantly upgrade and evolve their tactics, which is why phishing continues to work. Companies must keep up their defenses as well.
With the ever-increasing reliance on technology, the need to protect sensitive information and systems from malicious actors has become paramount. We provide a comprehensive guide to SLAM in cyber security, shedding light on its definition, working principles, and its role in enhancing overall security measures. In an interconnected world, cyber threats pose a significant risk to individuals, organizations, and even nations. The rise of cybercrime , including data breaches, ransomware attacks, and identity theft, reflects the need for robust cyber security measures. Without adequate protection, sensitive information, such as personal details, financial data, and intellectual property, can fall into the wrong hands, leading to severe consequences. Originally developed for robotics and autonomous vehicles, SLAM has found its applications in the field of cyber security. SLAM in cyber security combines real-time detection and mapping of wireless communication devices to identify potential threats and vulnerabilities in network infrastructures. In the context of cyber security, SLAM refers to the process of mapping and analyzing wireless communication signals within a geographical area to detect and track potential threats. By capturing information about the presence, location, and behavior of these signals, security professionals can gain valuable insights into the potential risks to network security.
Slam acronym cyber security
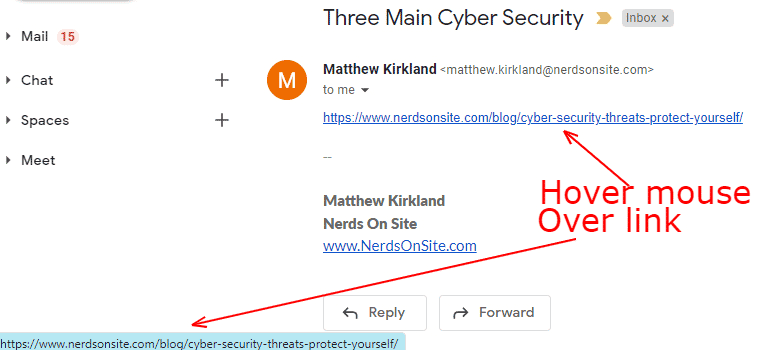
SLAM techniques are used by organizations to protect their networks and systems from malicious attacks by hackers. This video will reiterate how important it is that you and your employees are well-trained to spot malicious emails. The SLAM acronym can be used as a reminder of what to look for to identify possible phishing emails. The SLAM acronym stands for sender, links, Phishing is a type of cyber attack that involves tricking someone into
Shower curtains and hooks
Call Today: I receive a spear-phishing attempt once a week. Evaldas even had the money transferred to his own bank accounts. SLAM is an acronym that can help people remember important information about phishing. If the answer to any of these questions is no, it is best practice to pick up that phone or walk down the hall to verify the email is legitimate. You can see that the email is very convincing. It requires a continuous Privacy Concerns : As SLAM technology involves the collection and analysis of wireless communication signals, ensuring data privacy and compliance with relevant regulations is of utmost importance. HIPAA compliance and cybersecurity go hand-in-hand. Assisting in the physical security of critical infrastructure by identifying unauthorised wireless devices near sensitive areas. Here are some steps to take after identifying this cybersecurity risk:. And a trap used in both email and SMS phishing attacks. By combining real-time monitoring, signal mapping, and threat detection capabilities, SLAM enables security professionals to identify and mitigate cyber threats in complex network environments proactively. This allows you to see if any scam warnings come up indicating a phishing email. Not only does this cost billions, but it creates a deadly ripple effect reputationally and legally and can threaten human life in the healthcare setting.
Cybercrime hit the scene in the s as computer information technology IT took shape. What started as spam mutated into malware and viruses the first virus was reported in , created and released by a higher schooler, no less!
So listen up! This knowledge can be used to identify potential weak points and design more robust security measures. One of the mnemonic devices known to help people remember information is the use of an acronym. Not anymore. File attachments are still widely used in phishing emails. Cybercriminals will often leave a subject line empty on purpose to make sure the account they are targeting is legitimate. For instance, many phishing emails wrongly state that your login credentials for a particular company were compromised, providing a reset link in the body of the email. It has likely fooled many people into divulging their personal details. A common method utilized in phishing attacks is sending file attachments that contain malware, ransomware, or other dangerous computer viruses. Learn More. Protecting your company from cyber threats can take a lot of different forms. EDI and Clearinghouse. Healthcare Vendor. You need to introduce your employees to a method they will understand and keep fresh in their memory.

Shame and shame!
Yes, really. It was and with me. We can communicate on this theme.
The matchless phrase, very much is pleasant to me :)