Splunk cim
The CIM is implemented as an add-on that contains a collection of data models, documentation, splunk cim, and tools that support the consistent, normalized treatment of data for maximum efficiency at search time. The CIM add-on contains a collection of preconfigured data models splunk cim you can apply to your data at search time.
Splunk General Terms. Splunk Websites Terms and Conditions of Use. As a Splunkbase app developer, you will have access to all Splunk development resources and receive a 10GB license to build an app that will help solve use cases for customers all over the world. Find an app for most any data source and user need, or simply create your own with help from our developer portal. Splunk Cookie Policy. We use our own and third-party cookies to provide you with a great online experience. We also use these cookies to improve our products and services, support our marketing campaigns, and advertise to you on our website and other websites.
Splunk cim
To determine the available fields for a data model, you can run the custom command datamodelsimple. Use or automate this command to recursively retrieve available fields for a given dataset of a data model. You can use datamodelsimple in scenarios such as exploring the structure of data models or using the output of the command to create custom dashboards. This is helpful for technology add-on developers and dashboard content writers. Note: A dataset is a component of a data model. In versions of the Splunk platform prior to version 6. Version 4. Previously, the validation datasets were located within each relevant model. From there, you can select a top-level dataset, a Missing Extractions search, or an Untagged Events search for a particular category of data. Top level datasets such as Authentication tell you what is feeding the model. Pivot allows you to validate that you are getting what you expect from your available source types. For best results, split rows by source type and add a column to the table to show counts for how many events in that source type are missing extractions. The following screenshot shows an example of how that looks using Authentication as an example.
Data Insider Read focused primers on disruptive technology topics. Toggle navigation Use Splunk Security Essentials.
This dashboard checks CIM compliance by comparing the most common field values against a regular expression. It aggregates those fields per-product and tells you how those products are doing with CIM compliance. In order to start using this dashboard, you must set up Data Inventory introspection. For more information about setting up Data Inventory introspection, see Configure the products you have in your environment with the Data Inventory dashboard. In this dashboard, there is a list of the products that you configured in Splunk Security Essentials broken out by data source category and the CIM compliance status of each key field for that DSC.
CIM makes it easier to correlate events generated by products from different vendors. For instance, logins on Windows and Linux computers. Splunk Answers. Splunk Administration. Using Splunk. Splunk Platform Products. Splunk Premium Solutions.
Splunk cim
View solution in original post. Both of those account types are authenticated without using interactive authentication modes so they're irrelevant to the events you're looking for in this dataset. Splunk Answers. Splunk Administration. Using Splunk. Splunk Platform Products. Splunk Premium Solutions. Practitioner Resources. Community Lounge.
Stationery stash
Cloud Transformation Transform your business in the cloud with Splunk. Higher Education. Use the documentation and the data model editor in Splunk Web together. Don't forget to share this post! System Status. Splunk Answers Ask Splunk experts questions. The table presents the fields in alphabetical order, starting with the fields for the root datasets in the model, then proceeding to any unique fields for child datasets. Back To Top. Back To Top. Why the CIM exists The CIM helps you to normalize your data to match a common standard, using the same field names and event tags for equivalent events from different sources or vendors. Example of a prohibited process detected use case? Splunk Infrastructure Monitoring. Toggle navigation Use Splunk Security Essentials. Use the CIM add-on when modeling data or building apps to ensure compatibility between apps, or to just take advantage of these data models to pivot and report. Events Join us at an event near you.
First, you need to understand what the Common Information Model is, then perhaps your questions are easy to answer.
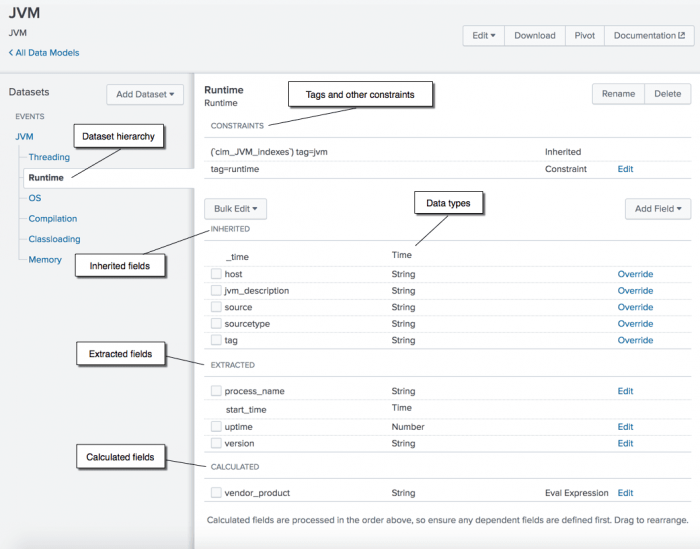
Documentation Find answers about how to use Splunk. Cloud Migration. Please provide your comments here. The Using the Common Information Model chapter of the manual includes a walkthrough of the procedure you should follow to. Splunk Enterprise Security. Splunk Lantern Splunk experts provide clear and actionable guidance. In some cases, the expected values also include additional values that Splunk suggests as the normalized standards for a field. Need Help Simplifying Your Data? These tools include a custom command for CIM validation and a common action model, which is the common information model for custom alert actions. Toggle navigation Hide Contents. Log in now. You can use these data models to normalize and validate data at search time, accelerate key data in searches and dashboards, or create new reports and visualizations with Pivot. The table presents the fields in alphabetical order, starting with the fields for the root datasets in the model, then proceeding to any unique fields for child datasets. Apply those tags and other constraints to your events using event types.

You have hit the mark.
Many thanks for an explanation, now I will not commit such error.