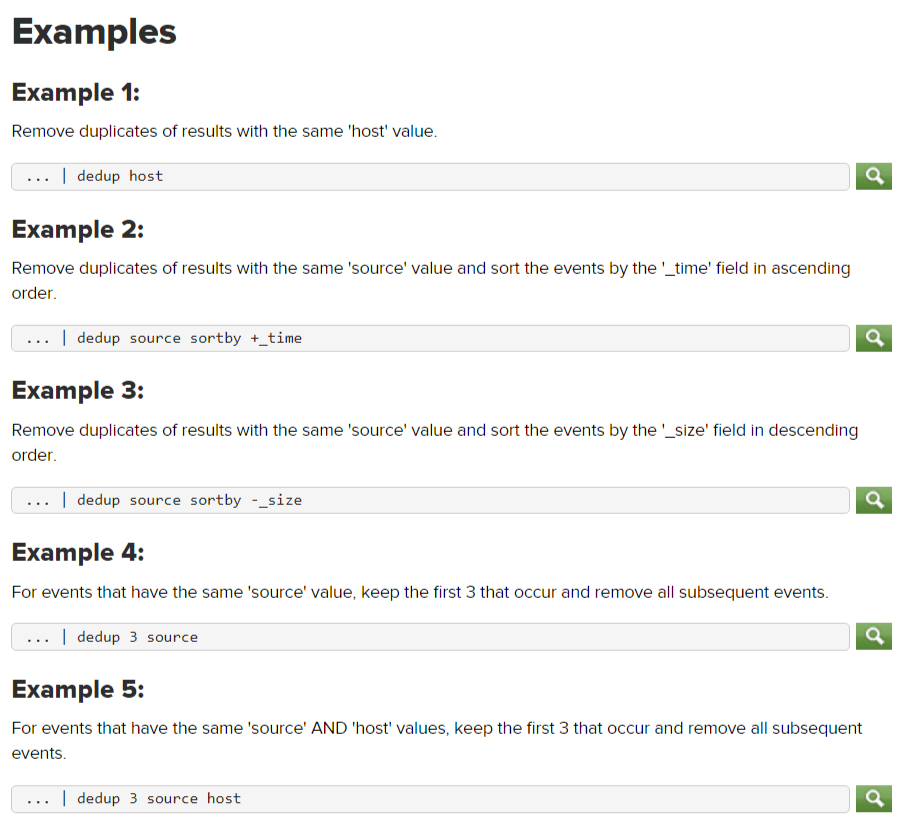
Splunk dedup
The following are examples for using the SPL2 dedup command.
Was this documentation topic helpful? Please select Yes No. Please specify the reason Please select The topic did not answer my question s I found an error I did not like the topic organization Other. Enter your email address if you would like someone from the documentation team to reply to your question or suggestion. Please provide your comments here.
Splunk dedup
The SPL2 dedup command removes the events that contain an identical combination of values for the fields that you specify. With the SPL2 dedup command, you can specify the number of duplicate events to keep for each value of a single field, or for each combination of values among several fields. Events returned by the dedup command are based on search order. For historical searches, the most recent events are searched first. For real-time searches, the first events that are received are searched, which are not necessarily the most recent events. You can specify more than one field with the SPL2 dedup command. For example:. Was this documentation topic helpful? Please select Yes No. Please specify the reason Please select The topic did not answer my question s I found an error I did not like the topic organization Other. Enter your email address if you would like someone from the documentation team to reply to your question or suggestion. Please provide your comments here. Ask a question or make a suggestion. Feedback submitted, thanks!
IT Modernization.
Sometimes in splunk I get a lot of duplicate results, is there a dedupe command I can use to narrow the results? View solution in original post. I'm having the same problem with dedup. Has anyone been able to use it without losing all results? Or maybe you have a different command that can help removing duplicates? I tried this and all of my results disappear and i have 0 results. I need all the duplicates also displayed in the table command.
Removes the events that contain an identical combination of values for the fields that you specify. With the dedup command, you can specify the number of duplicate events to keep for each value of a single field, or for each combination of values among several fields. Events returned by dedup are based on search order. For historical searches , the most recent events are searched first. For real-time searches , the first events that are received are searched, which are not necessarily the most recent events. You can specify the number of events with duplicate values, or value combinations, to keep. You can sort the fields, which determines which event is retained. Other options enable you to retain events with the duplicate fields removed, or to keep events where the fields specified do not exist in the events.
Splunk dedup
The following are examples for using the SPL2 dedup command. For search results that have the same source value, keep the first 3 that occur and remove all subsequent results. Use the order by clause in the from command to sort the events by time in ascending order, the default order. Sorting the events ensures that the oldest events are listed first. Remove duplicate results with the same source value. Only the oldest events are retained. For search results that have the same combination of source AND host values, keep the first 2 that occur and remove all subsequent results. Remove only consecutive duplicate events. Keep non-consecutive duplicate events. In this example duplicates must have the same combination of values the source and host fields.
Purple bricks rent
The SPL2 dedup command removes the events that contain an identical combination of values for the fields that you specify. Digital Customer Experience Deliver the innovative and seamless experiences your customers expect. Digital Customer Experience Deliver the innovative and seamless experiences your customers expect. Higher Education. Compatibility library for SPL commands. Splunk Dedup removes output which matches to specific set criteria, which is the command retains only the primary count results for each combination of values of specific fields and if the count isn't specified, it defaults to 1 and returns the result priory found. Version current latest release. Splunk Application Performance Monitoring Full-fidelity tracing and always-on profiling to enhance app performance. Big Data. Why not? Was this documentation topic helpful? Resources Explore e-books, white papers and more. Advanced Threat Detection. Result: Returned events, then stats counted.
Typical examples of a dedup produce a single event for each host or a pair of events for each sourcetype. Dedup has a pair of modes.
Feedback submitted, thanks! Community Share knowledge and inspiration. Custom eval functions Custom command functions Custom data types Documenting custom functions. Advanced Threat Detection. Compatibility library for SPL commands. Last modified on 20 October, AI and Machine Learning. Version Example SPL This is expected behavior. Splunk Infrastructure Monitoring Instant visibility and accurate alerts for improved hybrid cloud performance. There are several options available for dedup that affect how it operates. Financial Services. Is there a way I could combine the results from th

Also that we would do without your remarkable phrase