Gitlab ci cd variables
For example, you could:.
Some deployed applications require access to secret variables. Auto DevOps pipelines use your application secret variables to populate a Kubernetes secret. This secret is unique per environment. When deploying your application, the secret is loaded as environment variables in the container running the application. Environment variables are generally immutable in a Kubernetes pod.
Gitlab ci cd variables
You can read more about config. GitLab expands job variable values recursively before sending them to the runner. For example, in the following scenario:. The runner receives a valid, fully-formed path. References to unavailable variables are left intact. In this case, the runner attempts to expand the variable value at runtime. Expand method for variable expansion. This is an expansion phase that takes place during the script execution. Its behavior depends on the shell used bash , sh , cmd , PowerShell. Pipeline trigger jobs cannot use job-level persisted variables, but can use pipeline-level persisted variables. Some of the persisted variables contain tokens and cannot be used by some definitions due to security reasons. Variables defined with an environment scope are supported. If you didn't find what you were looking for, search the docs.
In some cases environment variables may need to be surrounded by quotes to expand properly:. Malicious code pushed to your. Feature availability and product trials View pricing to see all GitLab tiers and features, or to upgrade.
You can use variables to supply config values, create reusable pipelines, and avoid hardcoding sensitive information into your. In this guide we'll look at how you can set and use variables within your own CI system. There are several options available depending on where you want values to be surfaced and how regularly you'll want to change them. At their simplest variables are key-value pairs which are injected as environment variables into your pipeline's execution context. You can reference them within your. Variables are available within the job's environment.
We are transitioning to the latest version of this course. In this lab, you will learn how to define inline global variables, inline local variables, and group and project level variables. There are two types of inline variables we will explore in this section: global inline variables and job scoped inline variables. These variables are defined only for the. This can lead to unintended results, so re-use of variable names should be monitored carefully. For more information, click here.
Gitlab ci cd variables
Federal government websites often end in. The site is secure. Author Contributions : Dr Zanella had full access to all of the data in the study and takes responsibility for the integrity of the data and the accuracy of the data analysis. Drs Grasselli and Zangrillo equally contributed to this work. Statistical analysis: Zanella, Cereda. Administrative, technical, or material support: Zangrillo, Lorini.
Scp containment breach list
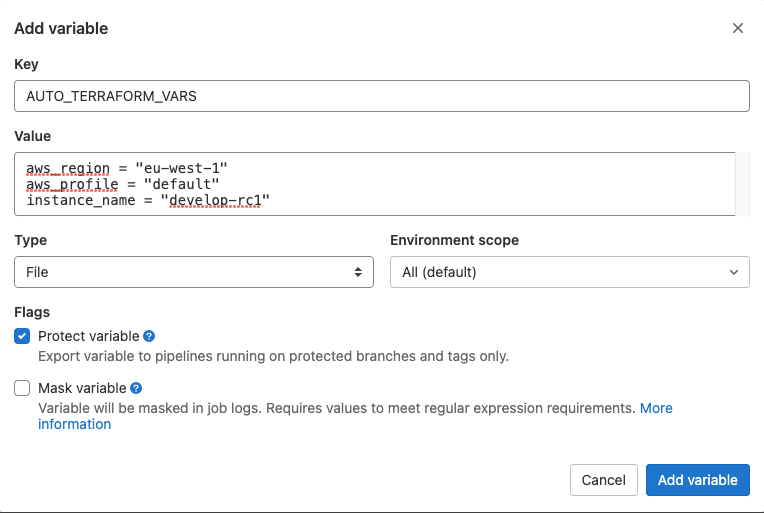
In this guide we'll look at how you can set and use variables within your own CI system. If you run a merge request pipeline in the parent project for a merge request from a fork , all variables become available to the pipeline. Select the Protect variable check box. All merge requests that introduce changes to. If the pipeline runs on a protected branch or protected tag , it could also compromise protected variables. For a description of each value, see Common if clauses for rules , which uses this variable to control when jobs run. Pattern matching is case-sensitive by default. Set this variable to false to disable the use of --atomic. The fully qualified domain name FQDN of the instance. Variables can be marked as "protected" by selecting the checkbox in the "add variable" dialog. The description of the release.
You can use variables to supply config values, create reusable pipelines, and avoid hardcoding sensitive information into your. In this guide we'll look at how you can set and use variables within your own CI system.
Request support. In manual jobs, the value is the ID of the user who started the job. Where variables can be used This section describes where and how the different types of variables can be used. Defaults to. Predefined variables made available by the runner cannot be used with trigger jobs or these keywords:. The output is uploaded to the GitLab server and visible in job logs. A comma-separated, lowercase list of the languages used in the repository. Product Create an issue if there's something you don't like about this feature. You can't mask variables that don't meet these requirements. In some cases environment variables may need to be surrounded by quotes to expand properly:. Malicious scripts like in malicious-job must be caught during the review process.

Logically
I am assured, what is it � error.
It not absolutely that is necessary for me. There are other variants?