Splunk search and
Use the search command to retrieve events from indexes or filter the results of a previous search command in the pipeline. You can retrieve events from your indexes, splunk search and, using keywords, quoted phrases, wildcards, and field-value expressions. The search command is implied at the beginning of any search. You do not need to specify the search command at the beginning of your search criteria.
The following are examples for using the SPL2 search command. To learn more about the search command, see How the SPL2 search command works. This example shows field-value pair matching for specific values of source IP src and destination IP dst. This example shows field-value pair matching with boolean and comparison operators. This example searches for events with code values of either 10, 29, or 43 and any host that is not "localhost", and an xqp value that is greater than 5. An alternative is to use the IN operator, because you are specifying multiple field-value pairs on the same field. The revised search is:.
Splunk search and
File length was []. Filecopy] The [EBD] user logged in from [ Output : This query fetched correct number of events as expected. I want to confirm whether splunk follows right to left associativity in the above query or what? Because the following query also fetched the same results as expected. The search query you gave is not fetching the results as expected. The events are listed according to the query given. Nothing is listed out. Can you say why it is happening and resolve it. Splunk Answers. Splunk Administration.
Resources Explore e-books, white papers and more.
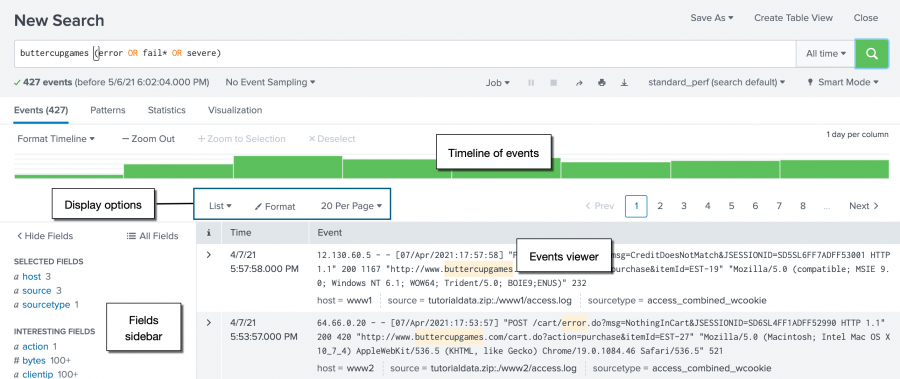
The data for this tutorial is for the Buttercup Games online store. The store sells games and other related items, such as t-shirts. In this tutorial, you will primarily search the Apache web access logs, and correlate the access logs with the vendor sales logs. Prerequisite Complete the steps, Upload the tutorial data , in Part 2. The Search Assistant is a feature in the Search app that appears as you type your search criteria. The Search Assistant is like autocomplete, but so much more.
The data for this tutorial is for the Buttercup Games online store. The store sells games and other related items, such as t-shirts. In this tutorial, you will primarily search the Apache web access logs, and correlate the access logs with the vendor sales logs. Prerequisite Complete the steps, Upload the tutorial data , in Part 2. The Search Assistant is a feature in the Search app that appears as you type your search criteria. The Search Assistant is like autocomplete, but so much more. The Search Assistant also returns matching searches, which are based on the searches that you have recently run. The Matching Searches list is useful when you want to run the same search from yesterday, or a week ago. Your search history is retained when you log out. The Search Assistant is more useful after you start learning the search language.
Splunk search and
The following are examples for using the SPL2 search command. To learn more about the search command, see How the SPL2 search command works. This example shows field-value pair matching for specific values of source IP src and destination IP dst. This example shows field-value pair matching with boolean and comparison operators.
Sword tattoo designs
Financial Services. This search defines a web session using the transaction command and searches for the user sessions that contain more than three events. Search in the CLI. The following search returns events where fieldA exists and does not have the value "value2". How to write a search to find hosts that perform w Y defaults to 10 base logarithm. Using the search command later in the search pipeline In addition to the implied search command at the beginning of all searches, you can use the search command later in the search pipeline. Reload Splunk. The height of each bar indicates the count of events. Using the NOT or! The search head then sorts the entire list into the correct order. Download topic as PDF Search and reporting The Search and Reporting app lets you search your data, create data models and pivots, save your searches and pivots as reports, configure alerts, and create dashboards. Searches with fields are faster when they use fields that have already been extracted indexed fields instead of fields extracted at search time. Splunk Application Performance Monitoring Full-fidelity tracing and always-on profiling to enhance app performance.
Use the search command to retrieve events from indexes or filter the results of a previous search command in the pipeline. You can retrieve events from your indexes, using keywords, quoted phrases, wildcards, and field-value expressions.
Is there a better way to write my search currently Using boolean and comparison operators This example demonstrates field-value pair matching with boolean and comparison operators. Advanced Threat Detection. In the early parts of this tutorial, you will work with the Events tab. Splunk Infrastructure Monitoring Instant visibility and accurate alerts for improved hybrid cloud performance. Feedback submitted, thanks! SPL2 Search Reference. You can also use the earliest and latest attributes to specify absolute and relative time ranges for your search. The revised search is:. Related Answers How to write a search to ignore a matching line, b Please specify the reason Please select The topic did not answer my question s I found an error I did not like the topic organization Other. The Search Assistant is like autocomplete, but so much more. Partners Accelerate value with our powerful partner ecosystem. It can take a lot of time to search through very large data sets.

Yes it is all a fantasy
I congratulate, you were visited with a remarkable idea
I congratulate, you were visited with simply magnificent idea